The Internet of Things is one of the most useful technologies of the present time. From offices to homes and factories to hospitals, IoT has connected the world in the most unimaginable ways. But these billions of connected IoT devices have also become a new point of entry for hackers. Without taking proper security measures, IoT devices can be easily exposed to security threats and other malware attacks. And as IoT is where the digital meets the physical world, the effects are therefore not limited to the digital world but can have disastrous effects in the physical world as well.
This article explains the three ways in which IoTConnect ensures the highest form of security.
1) Platform security
IoT platforms make development and deployment of IoT solutions easy. But another important role that they play is to ensure and enhance security. This helps in providing a secure foundation to build solutions, connect devices and transfer data. The focus is not to just maintain high-security levels for the platform but for the entire ecosystem.
Here is how IoTConnect as a platform ensures security;
- IoTConnect platform uses Azure services that provide built-in protection at every step of deployment
- API communication is very secure using HTTPS along with OAuth token for authenticating each request
- Secure HTTPS communication between microservices and user interface
2) Device security
Device security is an important step to ensure the overall security of an IoT setup. This assures that when connected IoT devices become part of an IoT ecosystem they can be fully trusted. The foundation of strong device security starts with offering a unique identity to every device.
Device identity
Device identity includes assigning a unique identifier to each device that helps to determine the behavior of the device, the way it communicates with other devices and the kind of security measures you need to take for that device. Building identity of IoT devices helps to build trust and ensure safety. Moreover, it makes authentication easy when any device goes online in the IoT ecosystem.
Authentication methods
Before we discuss the authentication methods used by IoTConnect, it is important to know the three major factors that need to be ensured during authentication:
- The device is genuine
- It is running a genuine software
- It is working on behalf of a trusted user
Here are the three device authentication methods used by IoTConnect to verify any device:
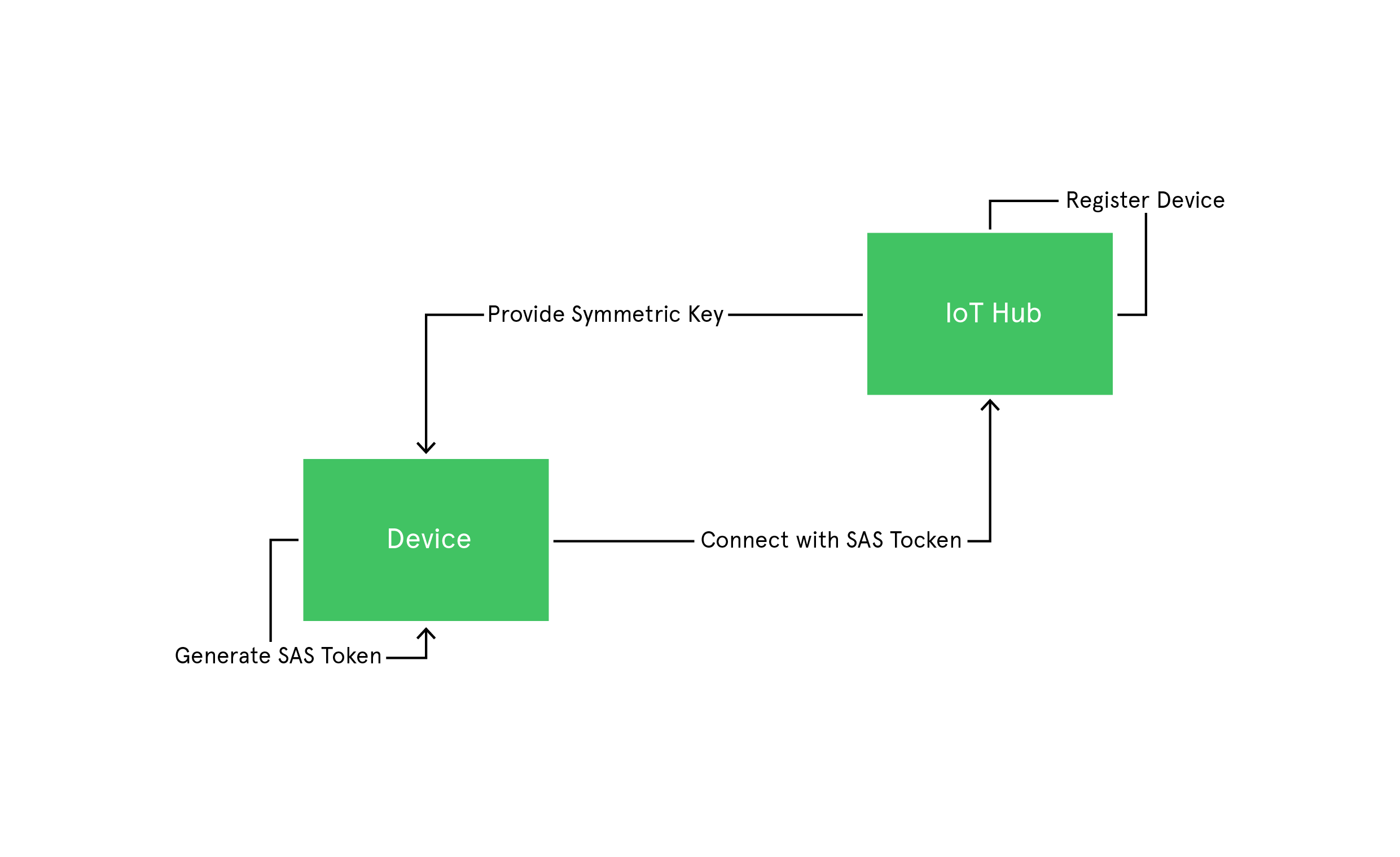
Key-based device authentication
It is one of the simple ways to authenticate any IoT device. Here, SAS tokens are generated using symmetric keys provided during device enrollment. The device then uses this key to generate SAS tokens. These SAS tokens have a hashed signature, which is used to verify the authenticity of these tokens. Once the device is authenticated, these SAS tokens are used to connect to Azure IoT Hub and send messages.
X.509 Certificates
X.509 certificate PKI is used to authenticate devices to IoT Hub and secure the IoT Hub endpoints. The process begins with registering and uploading X.509 certificates to an IoT Hub which will be used for authentication of IoT devices to the IoT Hub whenever they connect. This authentication process saves you from generating private secure keys for every IoT device. With X.509 CA feature, you need to register the certificate just once, and then use it to connect and authenticate as many devices as you want.
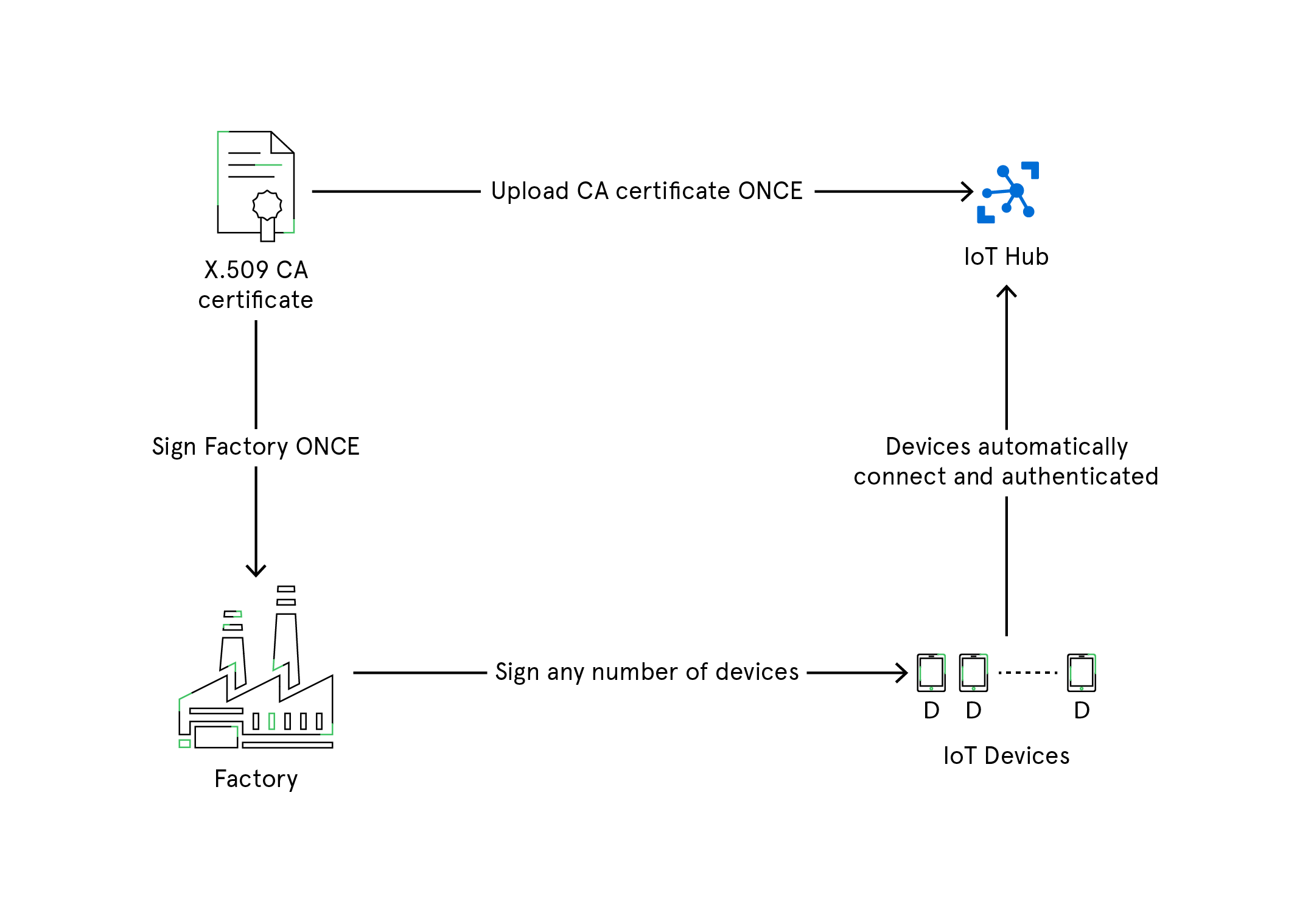
Trusted Platform Module (TPM)
Trusted Platform Module or TPM is another popular way to authenticate devices. It is a type of hardware security module (HSM) where a chip is injected into the motherboard of a device that stores cryptographic keys for authentication purpose. The public portion of the endorsement key contained in the TPM is used to recognize the genuine nature of a TPM and authenticate the device using device provisioning (DPS) service.
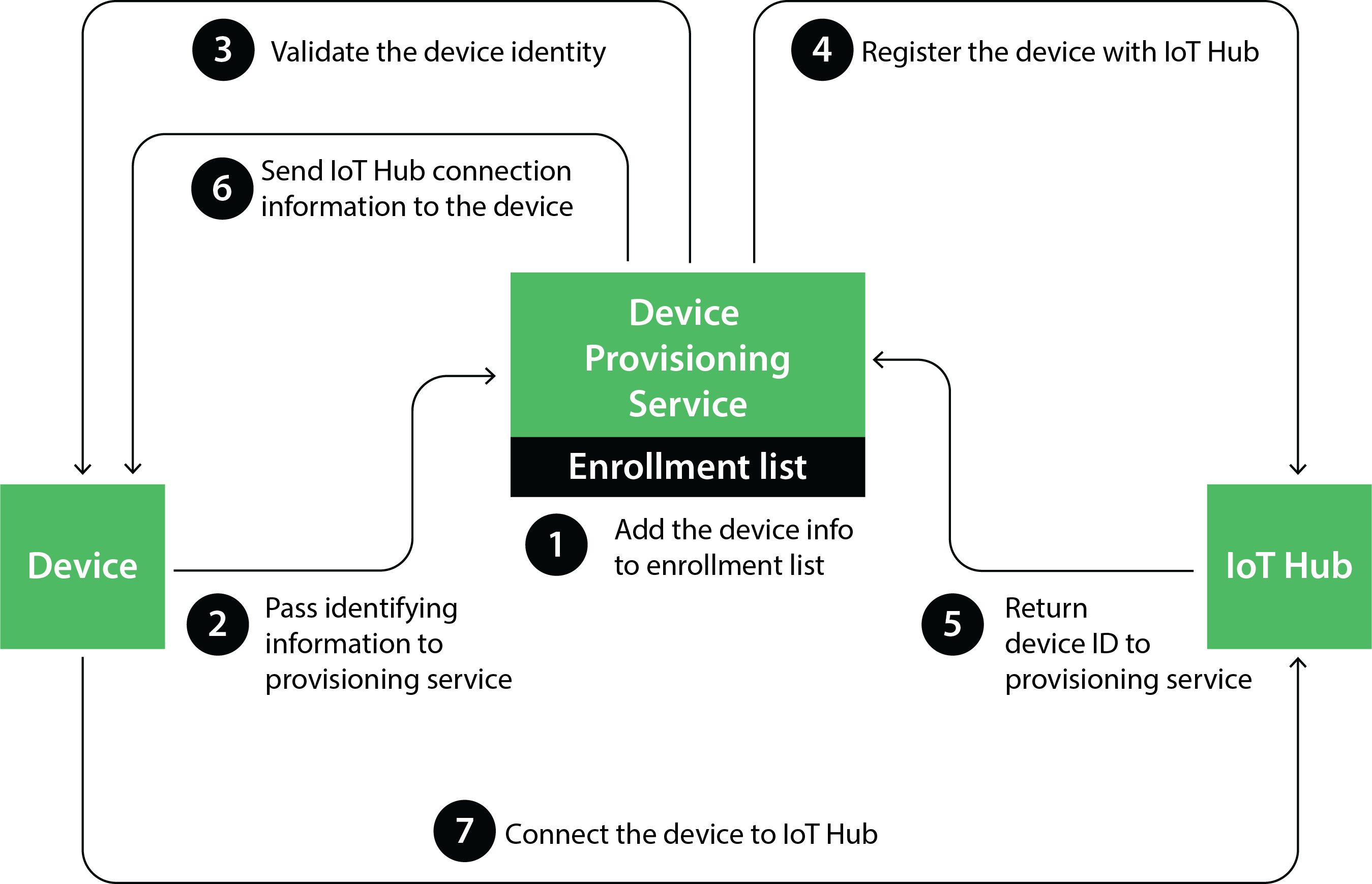
How TPM and DPS improve the authentication process:
- In case of the expiry of the security token used for secure connection with an IoT Hub, the device itself requests for a new token. This saves time from generating and assigning tokens every time they expire.
- As DPS has information about one or more IoT Hubs, it becomes easy to route the devices to the right IoT Hub.
The three authentication methods mentioned above are great to identify and authenticate a device. But it is recommended to use X.509 Certificates and TPM, as replacing symmetric keys is both hard as well as less secure.
3) Data security
Handling consumer data responsibly and protecting them against hacking and security breaches is important for every IoT platform. To process, transfer and store data securely, IoTConnect follows the below-mentioned steps:
- Secure communication
The communication mediums through which data is transmitted must be secured to avoid man-in-the-middle attacks and other types of intrusions. Our communication layer between the devices and IoT Hub is secured with Transport Layer Security (TLS) protocol. Moreover, IoT Hubs do not initiate any inbound connections as all the connections are initiated by authenticated devices only.
- Encrypted information
To add another layer of security, data is encrypted whenever it is transmitted among the entities (in transit). This helps to ensure that even if the data is ever intercepted when data transfer takes place it cannot be misused by anyone
- User authentication and authorization
Any user who wants to access the IoT ecosystem must be authenticated and identified. Once the authentication is completed, the next step is authorization where the user rights are determined. IoTConnect uses Azure Active Directory (AAD) for user authentication as well as authorization. This provides easy access management, safeguarding data against any malevolent actions by unauthorized users.
- Secure cloud layer
The cloud layer is where the data generated by the IoT devices is ingested, stored and analyzed. Therefore, it becomes important to have secure cloud services that can protect data from breaches. Data encryption facility is available for data stored in the cloud (at rest) which makes data secure in the cloud as well. Data is stored in Azure Cosmos DB which follows strict security guidelines. Moreover, there are several other ways to monitor data and raise alerts if any intrusion occurs.
To combat the security challenges that come along with an IoT ecosystem, IoTConnect uses the above-mentioned layered approach. This makes the infrastructure highly secure with minimal chances of being compromised.